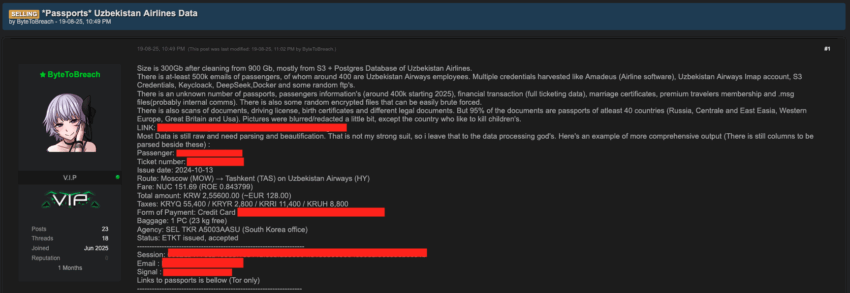
A hacker claims to have stolen information on hundreds of thousands of people — including U.S. government employees — after breaching an international airline. Straight Arrow News obtained a sample of the data, allegedly taken from Uzbekistan Airways, and confirmed the presence of sensitive documents such as scans of thousands of passports.
The data was advertised on Thursday by the hacker, who is known online as ByteToBreach and purports to be a native of the Swiss Alps, on a dark web forum known for hosting leaks, malware and hacking tools. The purportedly 300-gigabyte data cache contains, among other things, the email addresses of 500,000 passengers and 400 airline employees.
The post included a sample of the data, such as alleged credentials for multiple servers and software programs run by the airline. It also showed partial credit card data, as well as scans of 75 passports from the U.S., Russia, Israel, the U.K., South Korea and other nations. The hacker claims to have obtained identifying documents from more than 40 different countries.
The hacker provided Straight Arrow News with a larger data sample than the one posted online, containing 2,626 photos of identifying documents such as passports, IDs, marriage licenses and birth certificates. Numerous passports belonged to babies and young children.
Passports and other identifying data are valuable on underground markets given their potential use for a range of criminal activities, such as fraud and identity theft. Hackers could also leverage the prevalence of data on government employees for phishing attacks.
U.S. government employees’ data compromised
Another document from the sample the hacker provided to SAN contained 285 email addresses belonging to airline employees. A list of email addresses for passengers held 503,410 entries.
A spreadsheet with personal information of 379,603 members of Uzbekistan Airways’ loyalty program exposes names, genders, birthdates, nationalities, email addresses, phone numbers, member IDs and more.
The email addresses indicate that those members include employees of several U.S. government agencies, including the State Department, the Department of Energy, Immigration and Customs Enforcement, Customs and Border Protection and the Transportation Security Administration.
Employees of foreign government agencies from countries like Russia, Uzbekistan and the United Arab Emirates were also in the data.
SAN reached out to several phone numbers of government employees. An apparent TSA employee answered the phone by introducing themselves with the first name listed in the hacked data, as well as their government position. After SAN explained that their data had been exposed, the employee declined to comment and referred a reporter to the Department of Homeland Security’s public affairs office.
The public affairs office did not respond to an email from SAN. An email to the State Department’s office of press operations went unanswered as well.
Four files containing raw reservation and ticketing data mention airlines, airports, flight numbers and other information. The hacker also claimed that the raw data contained partial credit card information, although SAN was unable to independently verify the presence of financial data.
Hacker names a price
SAN also obtained screenshots from what the hacker claims are email exchanges with the airline. The hacker demanded payment from the airline in exchange for not selling the data online.
“If we don’t reach an agreement, I just exchange it with my buyers,” the hacker wrote. “I already notified them yesterday of what I have gathered. You should discuss this ‘situation’ first with your internal team, PR representatives and lawyers before making this decision.”
The hacker asked for the equivalent of 150,000 euros — roughly $176,000 — in bitcoin.
During the exchange, an airline employee acknowledged receiving attachments showing IDs taken from the company’s Amazon cloud storage server. The employee did not respond to an email from SAN.
On Thursday, however, the airline released a statement on its website denying any “unauthorized access to our information systems or any compromise of personal data belonging to passengers or employees.”
The airline claimed an internal review of the sample data suggested that it may have been generated with artificial intelligence.
“The examples cited in some publications as supposed proof of a leak are inaccurate and do not reflect reality,” the airline said. “The data mentioned in these materials bear no relation to our information systems and, according to preliminary assessments, may have been artificially generated or manipulated to create a false impression of an incident.”
The airline also urged “media representatives and users of online platforms” to “refrain from disseminating unverified information that may mislead the public and damage the airline’s business reputation.”
‘The truth is always in the data’
Web security consultant Troy Hunt, who runs the breach notification service Have I Been Pwned, told SAN that while hackers are known to fabricate breaches and organizations are known to deny legitimate intrusions, “the truth is always in the data.”
SAN emailed several people whose information was included in the sample data. One was a Russian man who provided a copy of a ticket from June when he used the airline to fly from Tashkent, Uzbekistan’s capital, to Moscow. A Japanese flyer confirmed joining the airline’s membership program in April. Others did not respond.
Uzbekistan Airways did not respond to inquiries from SAN.
Click this link for the original source of this article.
Author: Alan Judd
This content is courtesy of, and owned and copyrighted by, https://straightarrownews.com and its author. This content is made available by use of the public RSS feed offered by the host site and is used for educational purposes only. If you are the author or represent the host site and would like this content removed now and in the future, please contact USSANews.com using the email address in the Contact page found in the website menu.